Connectivity between ConfigMgr and Rimo3 resources
Connecting to on-premises ConfigMgr server using Site-to-Site VPN#
A Site-to-Site (S2S) VPN gateway connection is a connection over IPsec/IKE (IKEv1 or IKEv2) VPN tunnel. A S2S connection requires a VPN device located on-premises that has a public IP address assigned to it and a VPN Gateway in Azure.
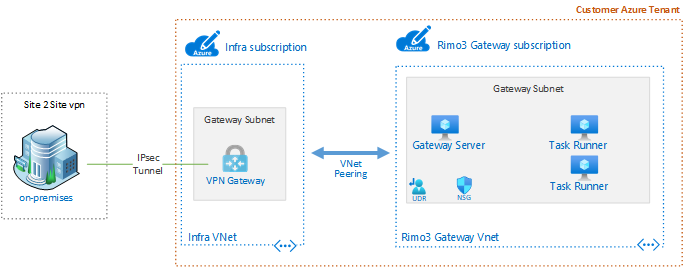
Once the S2S VPN is setup, as shown in the reference diagram Vnet peering needs to be enabled between Infra Vnet and Rimo3 Gateway Vnet.
Create, change, or delete an Azure virtual network peering | Microsoft Docs
info
An ExpressRoute Connection can be setup in place of S2SVPN. ExpressRoute lets you extend your on-premises networks into the Microsoft cloud over a private connection with the help of a connectivity provider.
Azure ExpressRoute Overview: Connect over a private connection | Microsoft Docs
Connecting to ConfigMgr server in Azure using Azure virtual network peering#
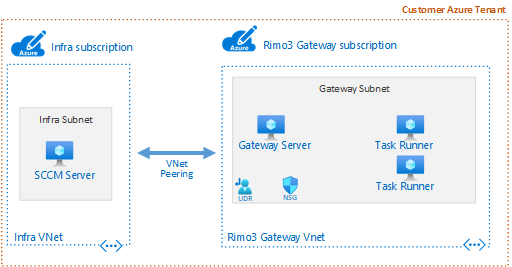
Building ConfigMgr server in Azure removes the dependency of S2S VPN / ExpressRoute connection. As shown in the reference diagram we just need to enable Vnet peering between Infra Vnet and Rimo3 Gateway Vnet.
Create, change, or delete an Azure virtual network peering | Microsoft Docs
IP Address Requirements#
- There shouldn't be overlapping IP address ranges if you are planning to implement Site to Site VPN\Express Route between your azure tenant and on-premises network.
- There shouldn't be overlapping IP address ranges for VNET peering between two Virtual networks